Beautiful things are coming your way, and it will be 314 soon.
Here is 11 things you need to know about Piπ and the mapping will be involved!
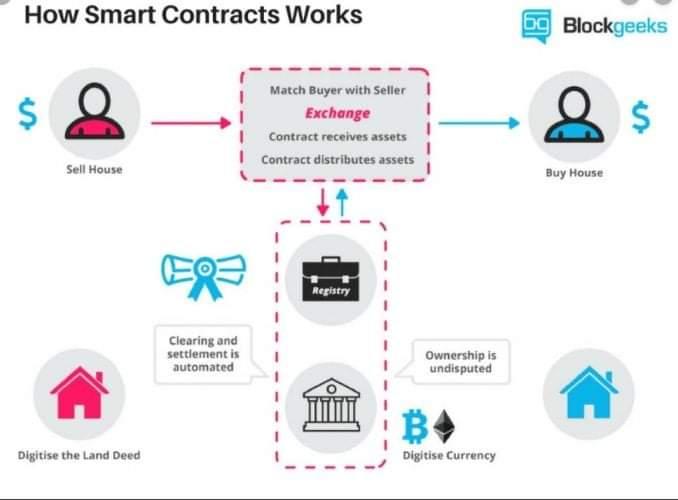
1. Smart contracts
A smart contract is a computer protocol designed to inform, verify, or execute a contract. Smart contracts allow for trusted transactions without third parties, which are traceable and irreversible.
2. Timestamp
Timestamp refers to a string or encoded information used to identify the date and time recorded. The international standard is ISO 8601.
3. Turing complete
Turing Complete refers to the ability of a machine to perform computations that any other programmable computer can perform. An example is the Ethereum Virtual Machine (EVM).
4. Dapp - Decentralized Application
is an open-source application that runs autonomously, stores its data on block L, incentivized in the form of cryptographic tokens, and operates with a protocol that shows proof of value.
5. DAO - Decentralized Autonomous Organization
Think of a company that operates without any human intervention and hands over all forms of control to an unbreakable set of business rules.
6. Distributed Ledger - Distributed ledger
Data is stored through a distributed network of nodes. A distributed ledger does not have to have its own token, it may be permissioned and private.
7. Oracle
An oracle is a trusted entity that introduces information about the state of the outside world through signatures, allowing deterministic smart contracts to react to an uncertain outside world. The oracle has the characteristics of immutability, stable service, and auditability, and has an economic incentive mechanism to ensure the power of operation.
8. Zero-knowledge proof
Zero-knowledge proofs were proposed by S. Goldwasser, S. Micali and C. Rackoff in the early 1980s. It refers to the ability of the prover to convince the verifier that an assertion is correct without providing any useful information to the verifier.
9. PrivateKey - private key
A private key is a string of data that is a token that allows you to access a particular dive. They act as passwords and are hidden from all but the owner of the address.
10. Public Key - public key
It is paired with the private key. The public key can calculate the address of the token, so it can be used as a credential to own the address of the token.
#Pi_Network_SD
Here is 11 things you need to know about Piπ and the mapping will be involved!
1. Smart contracts
A smart contract is a computer protocol designed to inform, verify, or execute a contract. Smart contracts allow for trusted transactions without third parties, which are traceable and irreversible.
2. Timestamp
Timestamp refers to a string or encoded information used to identify the date and time recorded. The international standard is ISO 8601.
3. Turing complete
Turing Complete refers to the ability of a machine to perform computations that any other programmable computer can perform. An example is the Ethereum Virtual Machine (EVM).
4. Dapp - Decentralized Application
is an open-source application that runs autonomously, stores its data on block L, incentivized in the form of cryptographic tokens, and operates with a protocol that shows proof of value.
5. DAO - Decentralized Autonomous Organization
Think of a company that operates without any human intervention and hands over all forms of control to an unbreakable set of business rules.
6. Distributed Ledger - Distributed ledger
Data is stored through a distributed network of nodes. A distributed ledger does not have to have its own token, it may be permissioned and private.
7. Oracle
An oracle is a trusted entity that introduces information about the state of the outside world through signatures, allowing deterministic smart contracts to react to an uncertain outside world. The oracle has the characteristics of immutability, stable service, and auditability, and has an economic incentive mechanism to ensure the power of operation.
8. Zero-knowledge proof
Zero-knowledge proofs were proposed by S. Goldwasser, S. Micali and C. Rackoff in the early 1980s. It refers to the ability of the prover to convince the verifier that an assertion is correct without providing any useful information to the verifier.
9. PrivateKey - private key
A private key is a string of data that is a token that allows you to access a particular dive. They act as passwords and are hidden from all but the owner of the address.
10. Public Key - public key
It is paired with the private key. The public key can calculate the address of the token, so it can be used as a credential to own the address of the token.
#Pi_Network_SD
Beautiful things are coming your way, and it will be 314 soon.
Here is 11 things you need to know about Piπ and the mapping will be involved!
1. Smart contracts
A smart contract is a computer protocol designed to inform, verify, or execute a contract. Smart contracts allow for trusted transactions without third parties, which are traceable and irreversible.
2. Timestamp
Timestamp refers to a string or encoded information used to identify the date and time recorded. The international standard is ISO 8601.
3. Turing complete
Turing Complete refers to the ability of a machine to perform computations that any other programmable computer can perform. An example is the Ethereum Virtual Machine (EVM).
4. Dapp - Decentralized Application
is an open-source application that runs autonomously, stores its data on block L, incentivized in the form of cryptographic tokens, and operates with a protocol that shows proof of value.
5. DAO - Decentralized Autonomous Organization
Think of a company that operates without any human intervention and hands over all forms of control to an unbreakable set of business rules.
6. Distributed Ledger - Distributed ledger
Data is stored through a distributed network of nodes. A distributed ledger does not have to have its own token, it may be permissioned and private.
7. Oracle
An oracle is a trusted entity that introduces information about the state of the outside world through signatures, allowing deterministic smart contracts to react to an uncertain outside world. The oracle has the characteristics of immutability, stable service, and auditability, and has an economic incentive mechanism to ensure the power of operation.
8. Zero-knowledge proof
Zero-knowledge proofs were proposed by S. Goldwasser, S. Micali and C. Rackoff in the early 1980s. It refers to the ability of the prover to convince the verifier that an assertion is correct without providing any useful information to the verifier.
9. PrivateKey - private key
A private key is a string of data that is a token that allows you to access a particular dive. They act as passwords and are hidden from all but the owner of the address.
10. Public Key - public key
It is paired with the private key. The public key can calculate the address of the token, so it can be used as a credential to own the address of the token.
#Pi_Network_SD